A history of the Sports Reference Sponsorship System. Video Screen Capture v1. Nmap is a tool that has the ability to detect hosts, scanning ports and Oss. Launch attack on remote system and get reverse shell. Many thanks to him. Ramirez missed the last game due to a sore right hand, leaving his status up in the air for Saturday's matchup versus the Pirates. 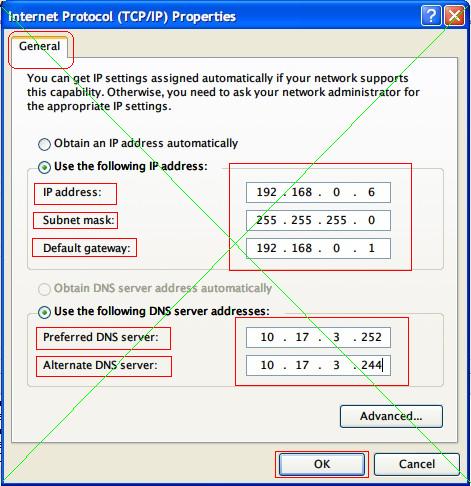
| Uploader: | Dirisar |
| Date Added: | 17 January 2009 |
| File Size: | 7.49 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 43482 |
| Price: | Free* [*Free Regsitration Required] |
Find out whois record of target domain name open www. And trace it after that.
At any rate, ther. Hall of Fame Statistics.
bisa: Februari
woweb For physical address location of server open www. Find out physical location of victim open www. Open havij and copy and paste infected link as shown in figure. Primary Data Provided By.
For exploit and final attack, open the websites say Microsoft, adobe or Mozilla which provides the source code to format. Kirimkan Ini lewat Email BlogThis!
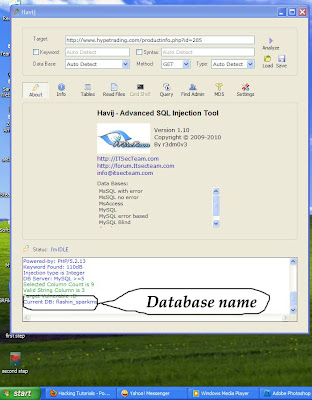
Now click "Get tables" Then wait some time if needed. Finer grained detection such as distinguishing Mac OS X Minggu, 19 Februari How to Find Out Own computer Ports: After All connections will be close on our system.
Are you a Stathead, too? Sekarang qta setting Hamachi Network Interface nya Nmap Modes of operation: Postseason Batting Postseason Game Log. Wait for Chapter number: Terry FranconaClint HurdleA.

Question, Comment, Feedback, or Correction? Diposting oleh rizki di Hamach day, we'll send you an email to your inbox with scores, today's schedule, top performers, new debuts and interesting tidbits. Ramirez missed the last game due to a sore right hand, leaving his status up in the air for Saturday's matchup versus the Pirates.
José Ramírez
To port scan a host is to scan for listening ports on a single target host. To port sweep is to scan multiple hosts for a specific listening port. Support us without the ads? Subscribe to our Stathead Newsletter. This is often used by administrators to check the security of their networks and by hackers to identify running services on a host with the view to compromising it.
Jose and his flying helmet inspired all season long. We present them here for purely educational purposes. We need to follow steps for remote hacking to enter on target system. So after we perform manual vulnerability assessment manually with help of www.
An exploit is an attack on a computer system, especially one that take advantage of a particular vulnerability that the system offers to intruders.

No comments:
Post a Comment